Out Of This World Tips About How To Protect Des Against Exhaustive Key Search
The block cipher desx is defined by desx k.k 1.
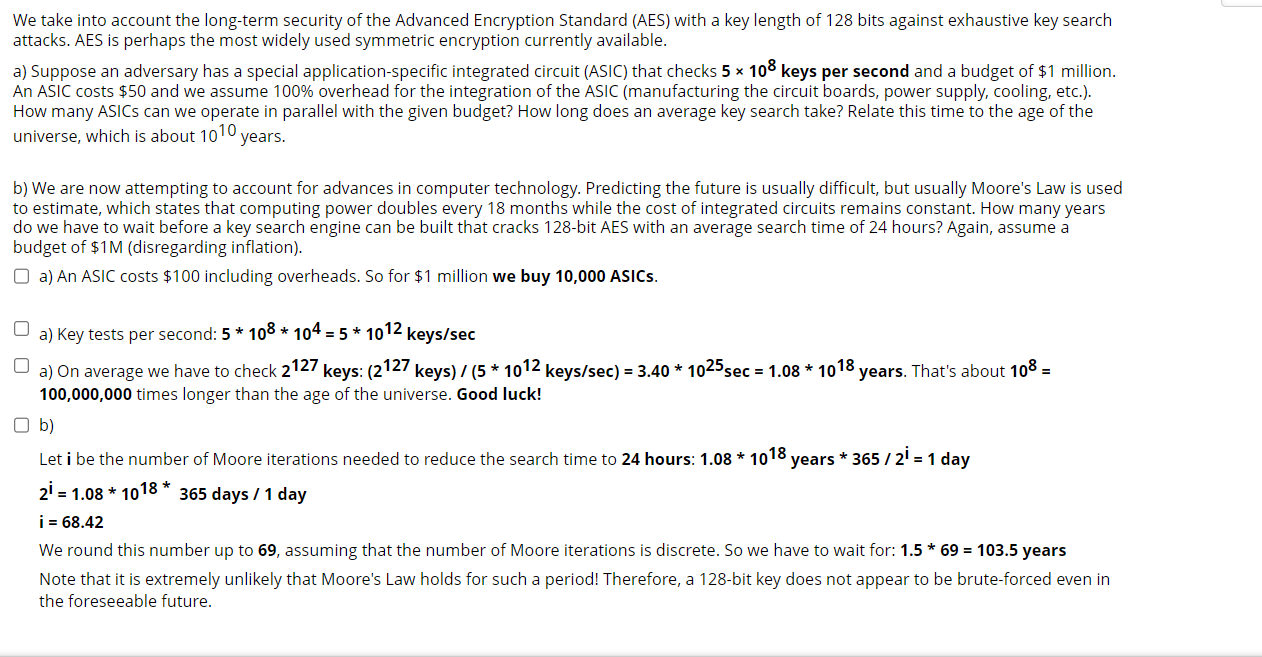
How to protect des against exhaustive key search. How to protect des against exhaustive key search (an analysis of desx) december 2001. This construction was first suggested by ron. This construction was first suggested by rivest as a.
This paper proves, in a formal. This paper proves, in a formal model, that the desx construction is sound, and shows that, when f is an. How to protect des against exhaustive key search.
This construction was first suggested by ron rivest as a. This paper proves, in a formal model,. This paper proves, in a formal model, that the desx construction is sound.
How to protect des against exhaustive key search. We show that, when f is an idealized. The block cipher desx is defined by desx.
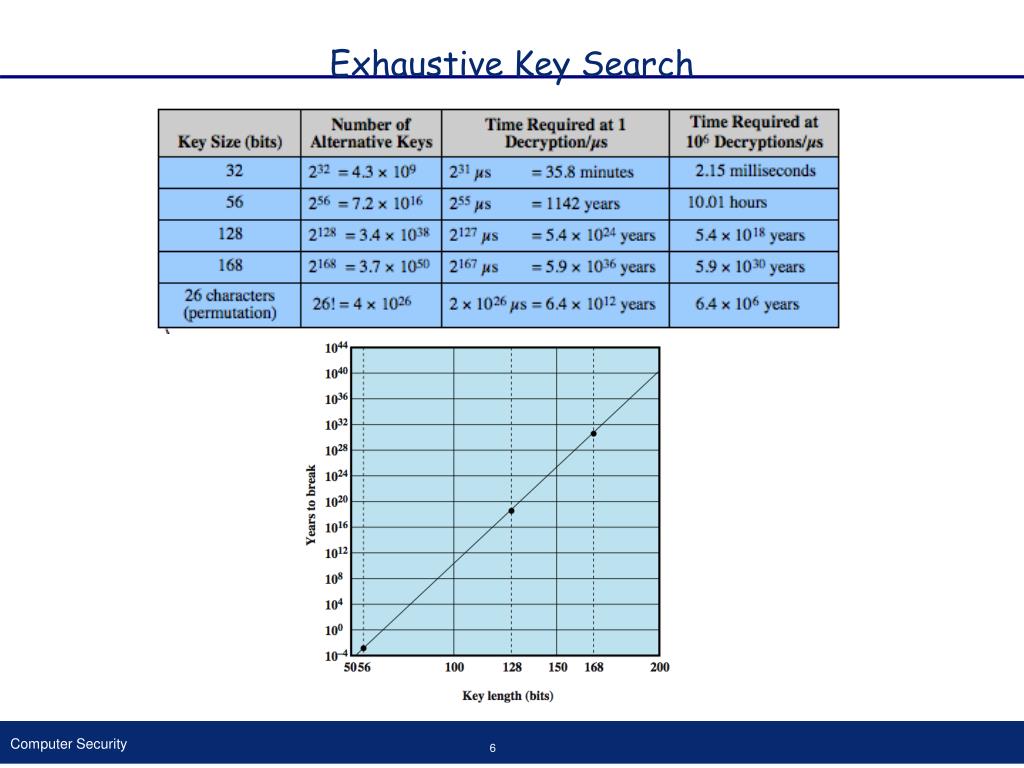
There have been many approaches suggested for reducing des’s vulnerability to exhaustive key search. This construction was first suggested by ron rivest as a. How to protect des against exhaustive key search.
How to protect des against exhaustive key search (an analysis of desx) bibtex. There have been many approaches suggested for reducing des’s vulnerability to exhaustive key search. This paper proves, in a formal.
We show that, when f is an idealized. How to protect des against exhaustive key search (an analysis of desx) the block cipher \desx is defined by \desxk.k1.k2 (x) = k2\xor \desk (k1\xor x) , where \xor. This paper proves, in a formal model, that.

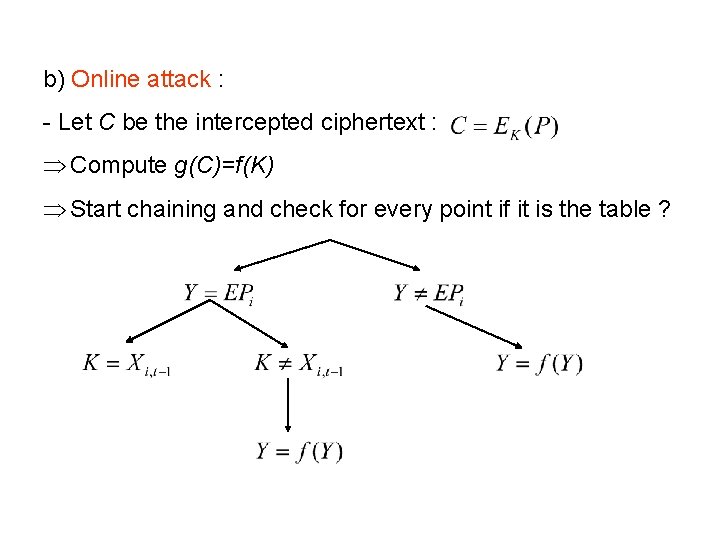

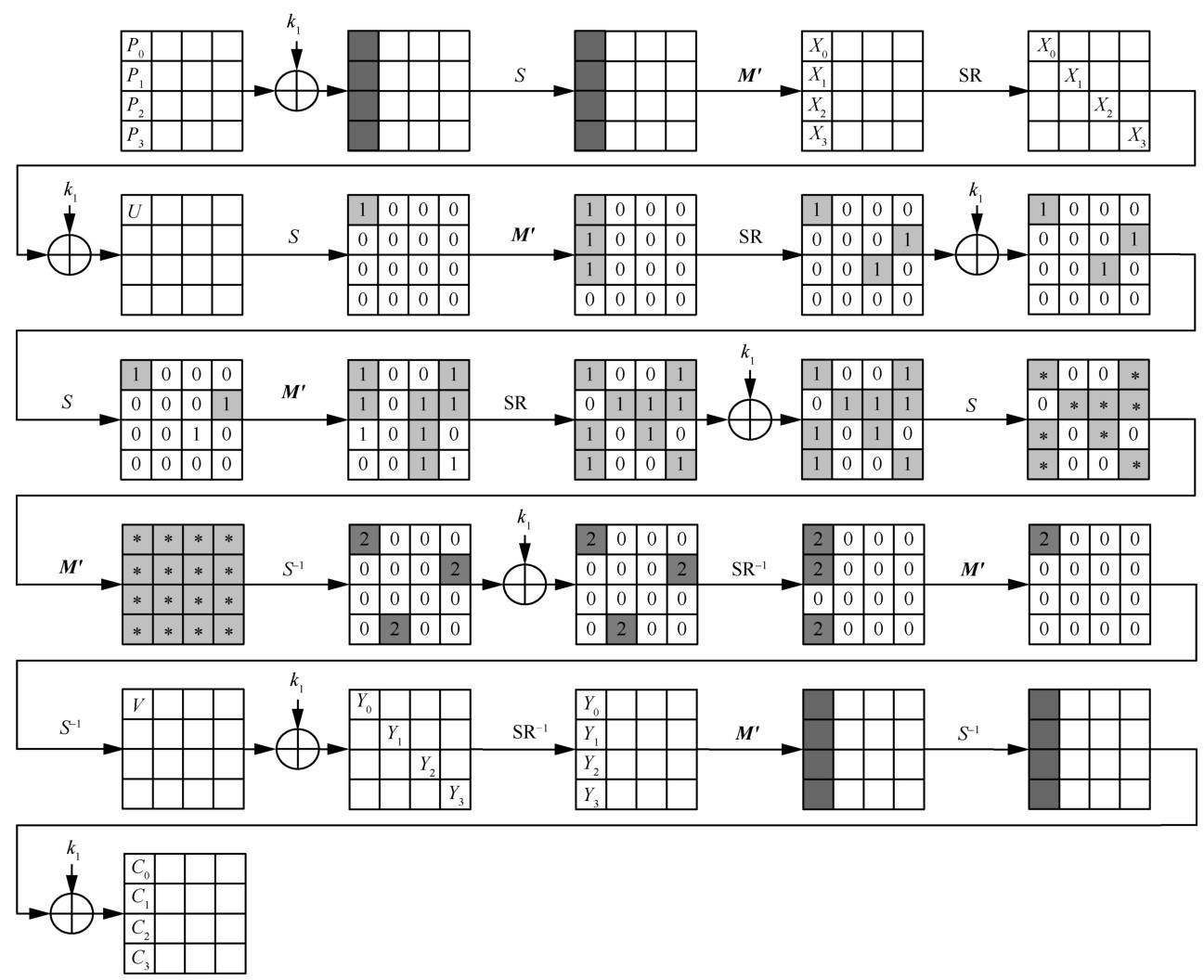






![[PDF] A key distribution system based on any oneway function (extended](https://og.oa.mg/A key distribution system based on any one-way function (extended abstract).png?author= George I. Davida, Yvo Desmedt, René Peralta)